Achieve OT security with ICS network visibility, operational insights, and threat detection
Cisco Cyber Vision delivers a powerful array of cybersecurity features to protect your OT network from security threats.
Whereas IND discovers and visualizes the connectivity of your industrial network devices, Cyber Vision maps and visualizes the traffic patterns between those devices (including the processing of native OT protocols). System baselines define normal network behavior and configuration, and when a deviation occurs, alerts are generated immediately, allowing quick mitigation of potential threats.
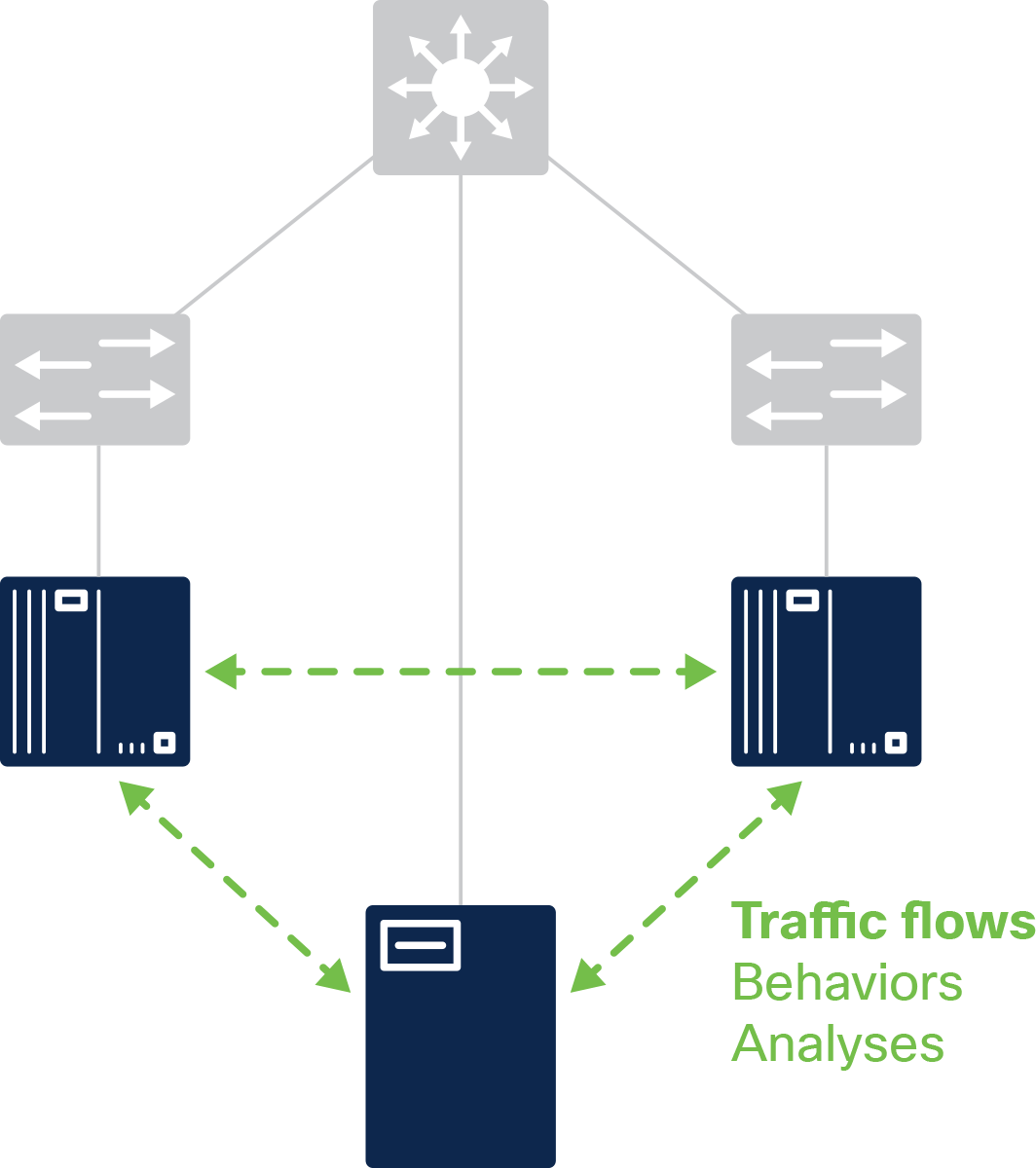
Cyber Vision allows OT personnel to group assets, providing the foundation of OT network segmentation. It also shares industrial asset context with other Cisco security solutions, giving your IT team unparalleled visibility into the OT environment.
Additionally, Cyber Vision provides insights into your OT security posture, risk scoring, device vulnerabilities, signature-based intrusion detection systems (IDS), and operational activities like configuration changes and control system events.
Cyber Vision deep packet inspection sensors are built into industrial-compute-capable Cisco switches, routers, and other network elements, lowering total cost of ownership (TCO).

A Malisko Customer Story
Using Cisco Cyber Vision, a manufacturer discovered several non-domain-joined Windows machines communicating with PLCs throughout its plant. The suspect machines turned out to be dual-homed laptops—connected via ethernet to its ICS and via Wi-Fi to its internet-enabled guest network. While intended for on-demand remote access for OEMs and Systems Integrators, this vulnerable connection could allow bad actors to directly access the production network from anywhere in the world.
This discovery served as a catalyst for the company to implement deeper segmentation and access policies, including an Industrial Demilitarized Zone (IDMZ). They used Cyber Vision to group OT devices by functional area, and pushed contextual information to Cisco Identity Services Engine (ISE) to develop and enforce security policy for the industrial zone.